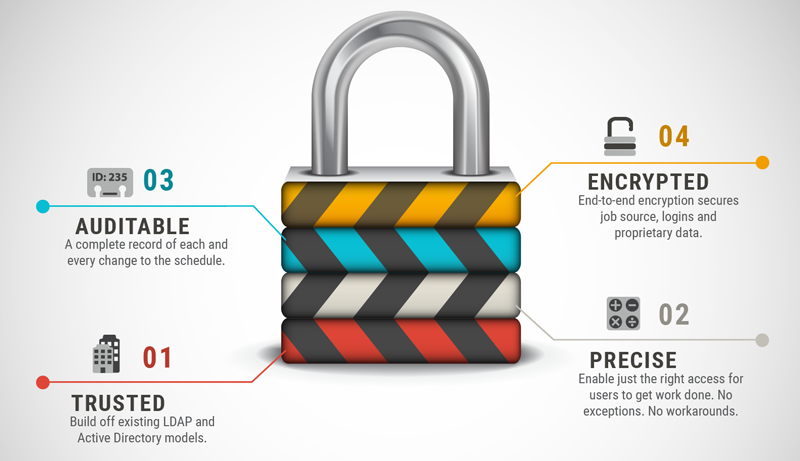
JAMS ensures that all sensitive user and password data is stored securely. Utilizing industry standard end-to-end encryption, JAMS secures any data being passed between hosts.
Granular Security Settings for Every Automator
The precise security controls in JAMS make it possible for individuals and teams of all types to leverage workload automation in accordance with an organization’s policies and procedures. These include:
- Non-IT Business Users – Eliminate IT order taking. Let business users submit jobs to the schedule on an ad hoc basis. Send managers actionable notifications about the status of their jobs.
- Developers and Contractors – Allow specific users to define, modify and monitor jobs that are relevant to their projects, while reserving the final deployment rights to your core IT team.
- Network Operations Centers – Maintain high availability. Provide users with limited access to the batch jobs they need to keep your environment running at peak performance.
Grant any combination of the following abilities to give just the right privileges to a user.
- Abort
- Change
- Control
- Debug
- Delete
- Inquire
- Manage
- Monitor
- Submit
Leverage Existing Security
By leveraging Active Directory Users and Groups you have one central location to ensure user access to JAMS is controlled. Why take chances with yet another set of logins, when you’ve already invested resources in centralized user management through Active Directory?